Trusted Platform Modules are computer chips that securely store artifacts used to authenticate the platform. These artifacts can include passwords, certificates, or encryption keys. You can also use a TPM to store platform measurements to make sure that the platform remains trustworthy. For servers configured with a Trusted Platform Module, TPM enables the firmware and operating system to take measurements of all phases of the boot process. For information on installing and enabling the TPM module option, see the user documentation for your server model. Secure Boot is a security standard developed by members of the PC industry to help make sure that your PC boots using only software that is trusted by the PC manufacturer.
It is supported on modern versions of Windows, and many distributions of Linux and variants of BSD. When the PC starts, the firmware checks the signature of each piece of boot software, including firmware drivers and the operating system. If the signatures are good, the PC boots, and the firmware gives control to the operating system.1Secure Boot does not encrypt the storage on your device and does not require a TPM. When Secure Boot is enabled, the operating system and any other boot media must be compatible with Secure Boot. Microsoft currently requires all Windows 8 certified platform vendors to provide secure boot functionality. While this might work fine for Microsoft and Apple, free OS vendors are not happy.
Linux implementations, for example, often do not include signing. Obtaining and managing code certificates is difficult, if not impossible, for decentralized and underfunded coding operations. While this is not typically a big problem for business desktop and mobile computing devices, it can cause problems for more technical users.
Further, it can possibly affect use of Linux-based appliances. Windows Security Center can be accessed in Windows 10 by searching for it in the Start Menu. When open, you can check under Virus and Threat Protection to see any threats or start a scan. Microsoft always updates the security intelligence in Windows Security Center, to ensure you're protected against the latest threats. You'll also be able to turn on real-time protection to ensure that downloaded malware won't run, and cloud-delivered protection to ensure that you get faster protections.
Does Tpm 2 0 Require Uefi You even can turn on controlled folder access to make sure that if your PC is hijacked by ransomware, critical folders won't be available for the ransomware itself. Trusted Platform Module 2.0 (TPM 2.0) and Secure Boot have both been around for a few years and most new Windows 10 computers will be running the security protocols by default. The technology combines special motherboard hardware in the form of chipsets with cryptographic security protocols to prevent malware from running before the Windows 10 operating system starts to boot. Before you check to see if you have TPM, PTT, or fTPM, you'll first want to upgrade your motherboard and UEFI BIOS firmware . Sometimes motherboard manufacturers will add specific features that will allow you to access these settings.
To do this, go to the motherboard manufacturer's website and download the necessary files. More often than not, the files you download will also include specific instructions for installing and upgrading. The Trusted Platform Module is a component of most modern computer systems.
It is used to help assure the integrity of the platform. It is used as part of the secure boot process to store and report on certain security metrics during the boot process. On some systems it is also used to securely store a full-disk encryption key.
If you enable this policy setting before turning on BitLocker, you can configure the boot components that the TPM will validate before unlocking access to the BitLocker-encrypted operating system drive. This chip is usually embedded on the motherboard, and it stores, generate, and protects encryption keys. Microsoft made this chip a prerequisite for upgrading to Windows 11, and if you are interested in this upgrade, you want to make sure that your device meets the requirements. Sometimes, TPM is disabled, which may give you the impression that your device is not ready for the Windows 11 upgrade. The great news is that you can easily enable it through UEFI.
There are two ways that you can go to the UEFI mode and enable TPM. When you change secure boot settings on an already encrypted system, you will see that bitlocker might switch to recovery mode, requiring you to enter the recovery key before you can continue booting. So as with all bios changes, it is recommended to suspend bitlocker before you do it. The primary scope of TPM is to ensure the integrity of a platform. In this context, "integrity" means "behave as intended", and a "platform" is any computer device regardless of its operating system.
This is to ensure that the boot process starts from a trusted combination of hardware and software, and continues until the operating system has fully booted and applications are running. UEFI benefits extend beyond memory and compatibility improvements. Limitations in MBR-based boot processes are resolved with the UEFI's use of the GUID Partition Table . The GPT uses globally unique identifiers to address partitions, allowing booting from disks as large as 9.4 ZB [9.4 x 1021 bytes] . Further, the UEFI allows more platform boot options, including network boot capabilities, and can act as the foundation for extended boot loaders. Storage limitations disappear, and boot processes can retrieve data and program modules from anywhere on installed storage.
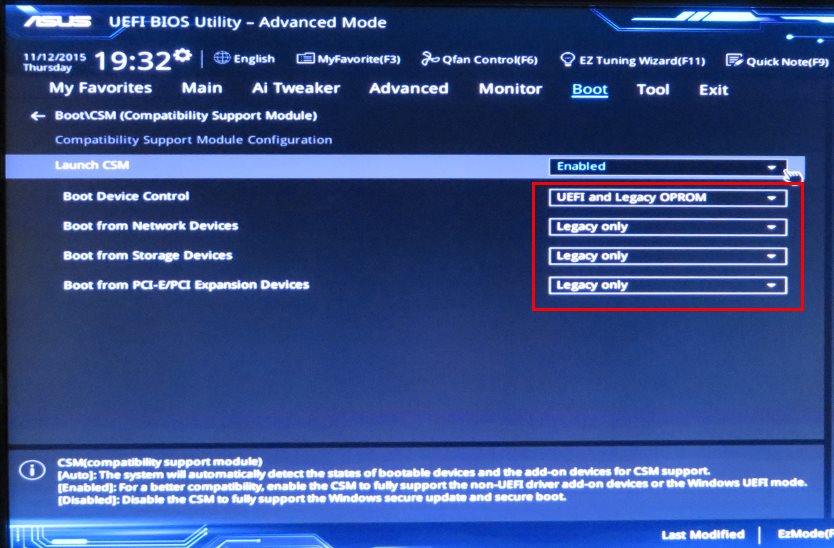
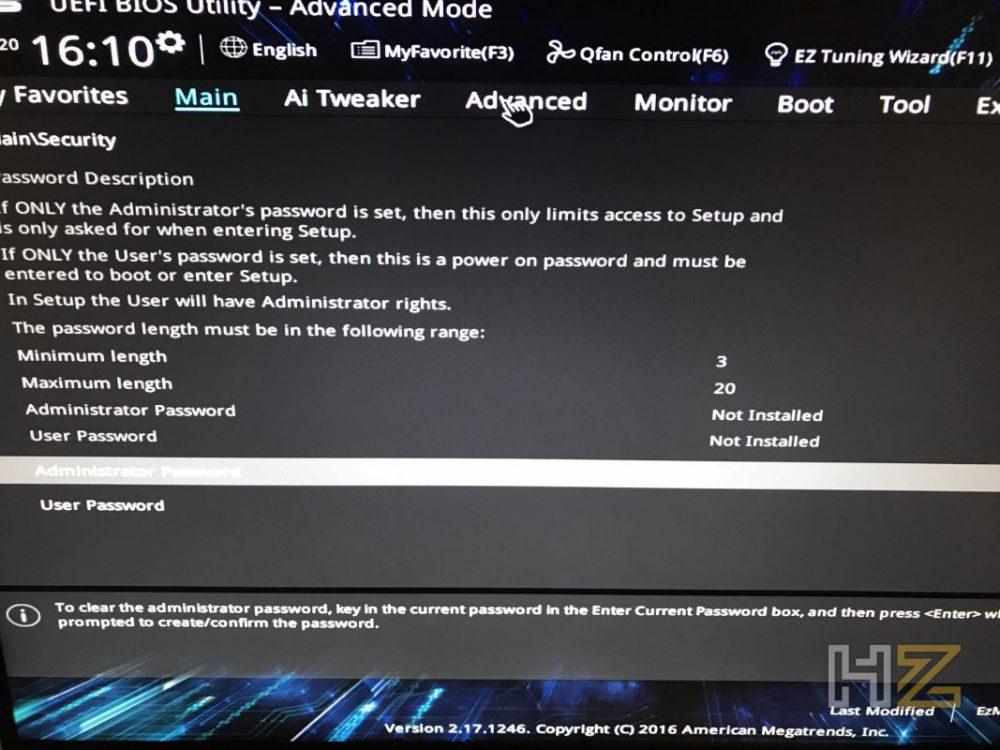
An OS that is using TPM might lock all data access if you do not follow proper procedures for modifying the server and suspending or disabling TPM in the OS. This includes updating system or option firmware, replacing hardware such as the system board and hard drive, and modifying TPM OS settings. Changing the TPM mode after installing an OS might cause problems, including loss of data. If you don't have access to the Windows 10 desktop, or this is a new computer, you can access the UEFI settings to enable a trusted platform module during the startup process. Secure Boot Mode standardCustom would allow us to set the keys used for attestation for Secure Boot. The final step before enabling Secure Boot is actually saving all our settings and restarting, because we need to boot the machine with CSM disabled before we can enable Secure Boot.
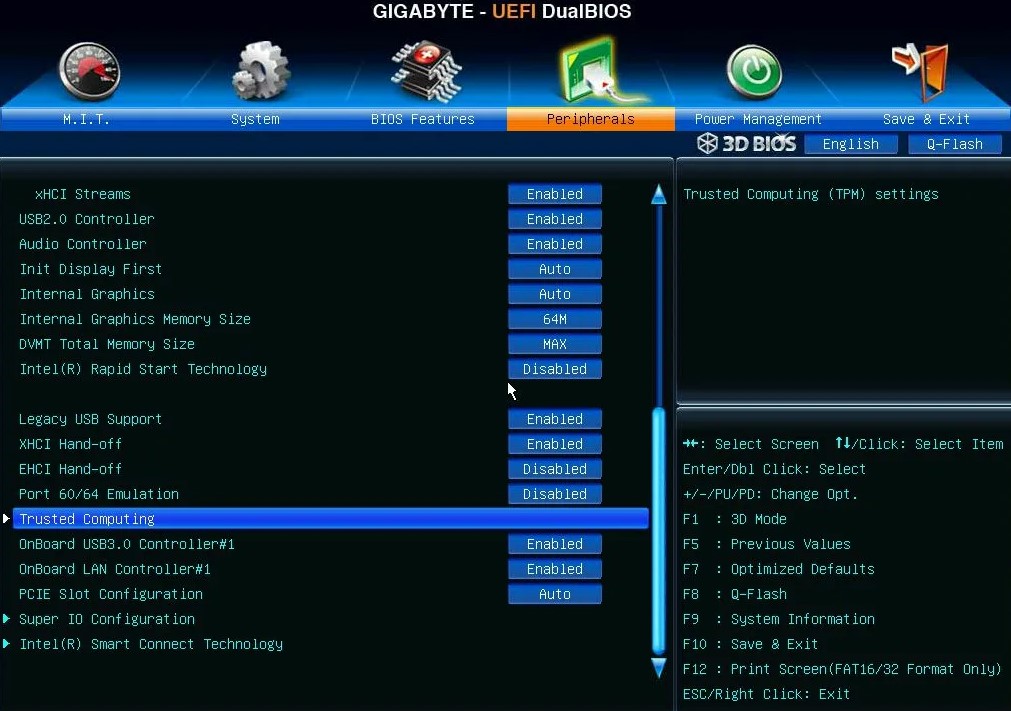
After switching on the computer and before the boot process, press the Key to enter the BIOS. On most PCs this is the "Remove", F2 or F12 key, but there are also PCs with a different setting. In the BIOS you then switch to the UEFI by calling up "Advanced Mode" or similar, and then to the "Advanced – Trusted Computing" area. On some computers you can also find the required option under "Miscellanous" or "Security". TPMs are controversial among security specialists and governments.
An updated and enabled TPM is a strong preventative against firmware attacks, which have risen steadily and drawn Microsoft's attention. However, it also allows remote attestation and may restrict the kinds of software your machine is allowed to run. TPM-equipped machines generally aren't shipped in countries where western encryption is banned. In Russia, TPM use is only allowed with permission from the government.
First, take note of the make and model of the machine that you are going to prepare. Many manufacturers update their device's UEFI support and update the system settings menu choices with firmware updates, so consider updating to the latest version. Once you've got a dual-boot, it's not too hard to switch between the two operating systems.
Hit the Windows key to pull up the Start menu, type UEFI and pick Change advanced startup options, then select Restart now. Once you boot back into the advanced startup menu, pick Use another operating system and it'll present you with your choice of OS. A Trusted Platform Module chip is an essential piece of hardware that is a prerequisite for a Windows 11 Upgrade. If you have a relatively new computer, it is most likely that it has a TPM chip. However, even if your computer has a TPM chip, it doesn't mean it is enabled.
This TPM chip is not only essential for a Windows 11 upgrade. You also need it for security features like BitLocker and device encryption. In this tutorial, I will show you how to enable TPM 2.0 Chip on your PC if it's supported. But it's not as simple as buying a TPM 2.0 add-on module and plugging it into the header. Even if you've got a hardware TPM installed in your home-built computer, you'll need to ensure that it's properly set up in the BIOS for the Windows operating system to recognize it. This process varies widely based on which motherboard and CPU you're using.
Even Microsoft acknowledges that turning on TPM isn't necessarily a straightforward process. Microsoft VP of Product Management Steve Dispense suggests that it may be necessary to enable a setting like Platform Trust Technology in the BIOS of Intel-based computers, or fTPM for AMD-based ones. Many motherboards come with a cluster of header pins clearly labeled "TPM." And, as ExtremeTech notes, you can pick up a TPM module for some motherboard models for less than $50. At its most basic, the TPM is a tiny chip on your computer's motherboard, sometimes separate from the main CPU and memory. The chip is akin to the keypad you use to disable your home security alarm every time you walk in the door, or the authenticator app you use on your phone to log in to your bank account. In this scenario, turning on your computer is analogous to opening the front door of your home or entering your username and password into the login page.
If you don't key in a code within a short period of time, alarms will sound or you won't be able to access your money. The TrueCrypt disk encryption utility, as well as its derivative VeraCrypt, do not support TPM. As such, the condemning text goes so far as to claim that TPM is entirely redundant.
The VeraCrypt publisher has reproduced the original allegation with no changes other than replacing "TrueCrypt" with "VeraCrypt". The author is right that, after achieving either unrestricted physical access or administrative privileges, it is only a matter of time before other security measures in place are bypassed. However, stopping an attacker in possession of administrative privileges has never been one of the goals of TPM (see § Uses for details), and TPM can stop some physical tampering. Platform-specific specifications define what parts of the library are mandatory, optional, or banned for that platform; and detail other requirements for that platform. Platform-specific specifications include PC Client, mobile, and Automotive-Thin.AlgorithmsSHA-1 and RSA are required. Triple DES was once an optional algorithm in earlier versions of TPM 1.2, but has been banned in TPM 1.2 version 94.
Many other algorithms are also defined but are optional. Symmetric-key algorithms and exclusive or are optional. It permits the ANDing and ORing of these authorization primitives to construct complex authorization policies. This enables security features that can help protect your computer like encrypting your storage drives or using logins like fingerprints or facial recognition. This is only possible because there's a safe place on your computer to store the encryption keys or biometric data that wouldn't be safe to store otherwise. In addition to PCRs, module storage consists of VRAM and NVRAM (non-volatile memory) (Du, Li, & Shen, 2011).
NVRAM contains hardware-protected root of trust data necessary to execute and assure boot path measurements. In addition, it contains certificates necessary for attestation of signed operating system files and firmware. Conversely, VRAM contains command parameters and is subject to operational changes. Each of these components, or component groups, plays an important UEFI support role.
The RSA Engine can create one-time symmetric keys of up to 2048 bits. It is used during key wrapping operations, digital signing, and encrypting large blocks of data. The SHA-1 (or SHA-256) engine hashes large blocks of data. RNG is a module's random number generator used to generate keys. The AIK is bound to the platform on which the module resides.
It is an asymmetric key pair that attests to the validity of the platform's identity and configuration. There are 24 Platform Configuration Registers , many of which are used to store measures created during the UEFI boot process. PCRs are write-only and cleared only on platform reset. However, it is noteworthy that many of the default features being deployed in Windows 11 are available as options in Windows 10. In some cases, getting these more advanced levels of security is just a matter of turning them on.
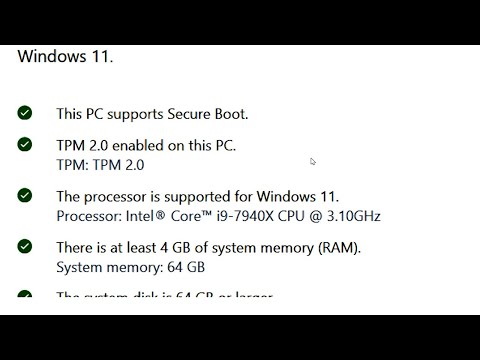
In other cases, your PC's hardware may be too old to handle the new security requirements. In some cases, especially if your PC was purchased in the past few years, these advanced security settings may be installed and active in the background right now. So, if you don't have a hardware TPM chip, there may be an option to enable fTPM. Windows 11 now lists TPM 2.0, Secure Boot, and UEFI mode as mandatory options to run it. While modern motherboards support all three of those, for some reason, manufacturers ship their products with TPM and Secure Boot disabled by default. Microsoft has made a new tool for checking Windows 11 compatibility.
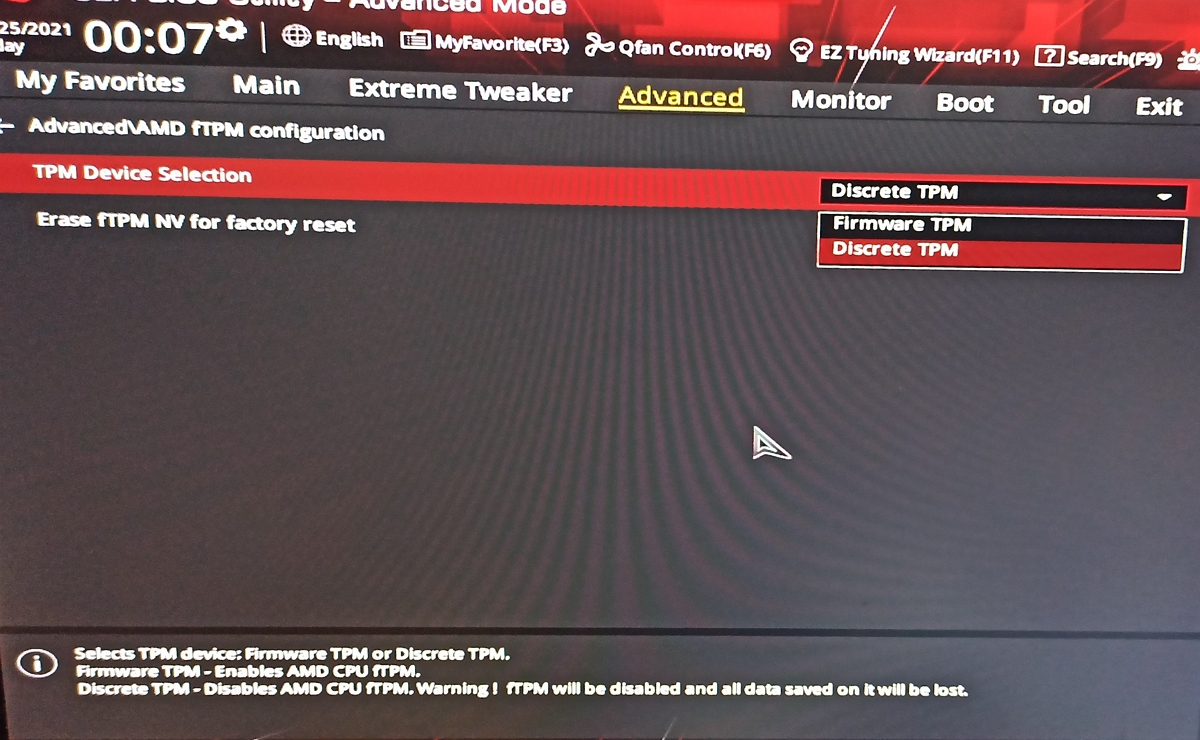
If Trusted Platform Module and Secure Boot are disabled on your machine, the compatibility check tool will tell your PC is not eligible to run Windows 11, even with the newest hardware. Since announcing Windows 11 requires TPM 2.0, a few articles have been written about how scalpers are selling TPM chips for significantly over MSRP. Thankfully, recently AMD and Intel chips support a firmware based TPM that can be enabled in the motherboard settings. The setting is called AMD fTPM or Intel Platform Trust Technology .
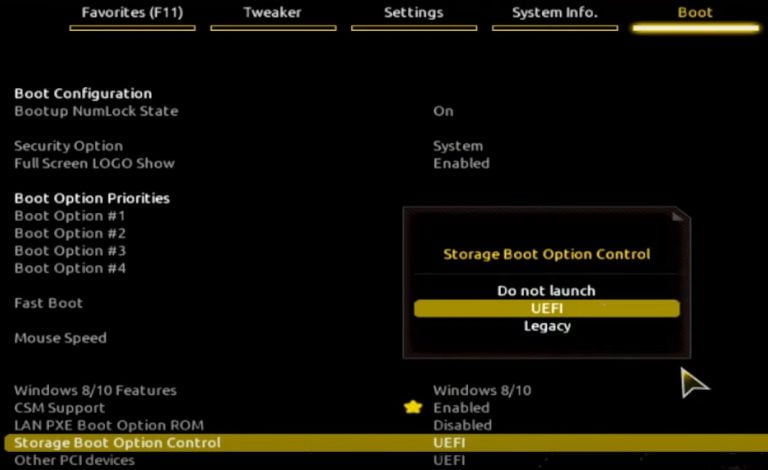
In addition, some of the users reported enabling Virtualization in BIOS help them fix the issue and their computer allows install windows 11 without any error. So look for "Intel Virtualization Technology" or "Virtualization Technology" or "Intel VT-x" or "AMD-V" or "SVM Mode" in your BIOS settings If found anything just enable it. To change the boot mode highlight the boot mode option then press enter key, now choose UEFI from the options.
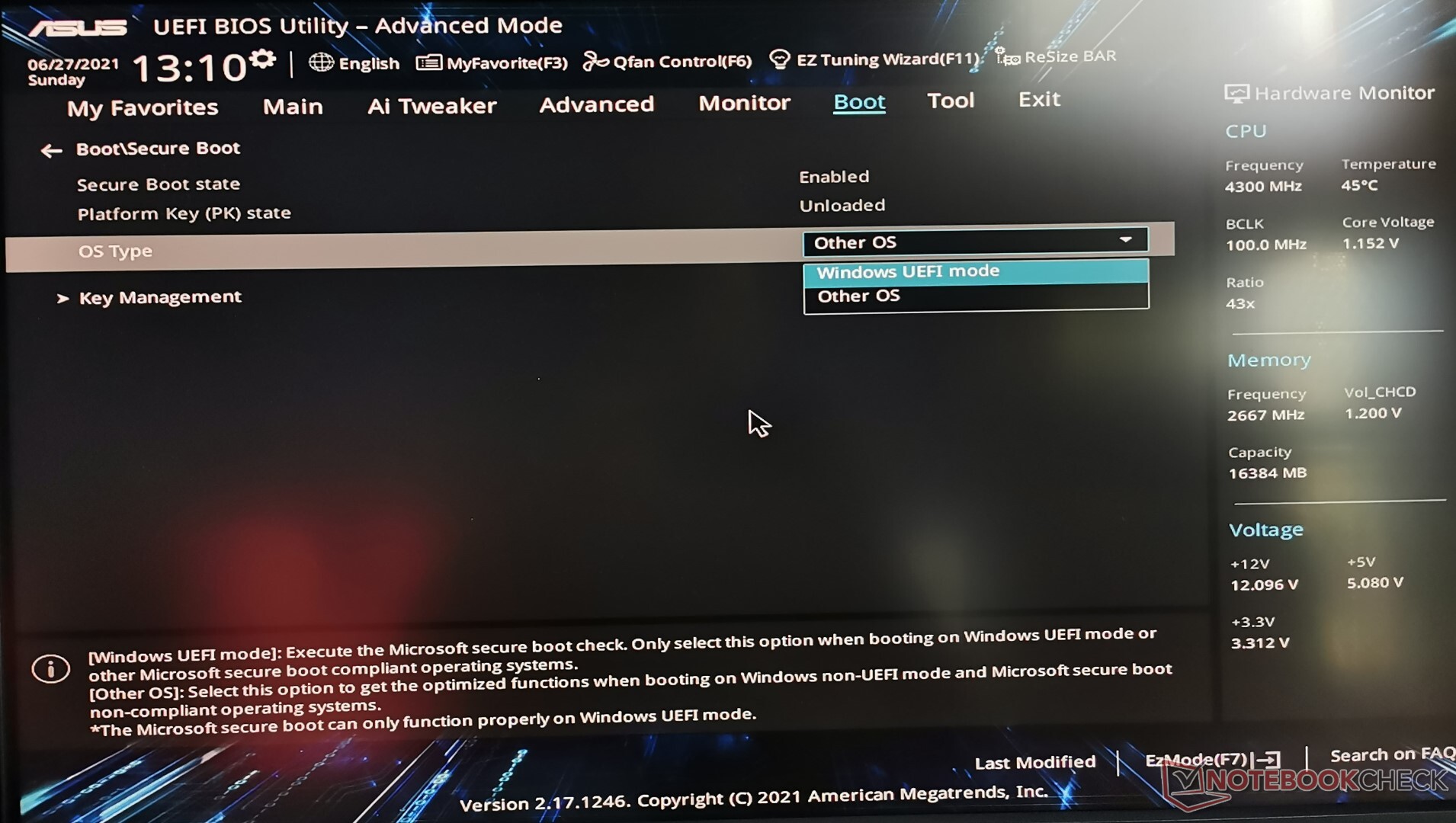
(Use the up and down arrow keys to select UEFI and hit enter to select the option. UEFI is very similar to BIOS and is essential for connecting a computer's firmware to its operating system. Secure Boot is a set of programs that check whether your operating system is secure for running on a machine. And installing Windows using the newer UEFI mode is recommended as it comes with more security features such as Secure Boot than the legacy BIOS mode.
The problem becomes even more significant for those running virtual machines. Several virtualization platforms default to BIOS rather than UEFI boot for guests. It's simpler, it generally boots quicker, and it has been around a lot longer. If your daily driver Windows 10 VM is booting from BIOS, you'll be stuck with the same can't-get-there-from-here issues that PC builders who selected a BIOS boot had.
You can check to see if your PC has secure boot enabled by going to the Start Menu and typing msinfo32, and then pressing enter. The System information page will open, so click on System Summary on the left. From there, look to the middle right side of the screen. If Secure Boot State reads Off, then Secure Boot is available, but disabled. Once here, you can also enable Secure Boot from the UEFI menus.
If your system only supports a firmware-based TPM, it might be referred to as iPPT if your computer has an Intel processor, or fTPM for AMD processors. Fortunately, the most recent version will tell you if TPM is the problem. You might run into this issue if you built your PC yourself or got someone else to do it for you. Many motherboards are TPM compatible, but some gaming motherboards skimped on the feature in favor of other bells and whistles.